While having a website hacked may be just a minor headache for a beginner blogger, it’s a major disaster for a business. For example, if an online company possesses private or sensitive customer data, losing it to hackers is a nightmare that could lead to a reputation blow, fewer sales, and, in some cases, legal consequences.
That’s why many entrepreneurs, bloggers, and other people looking to establish their own website ask this question:
“Is WordPress secure enough?”
Well, one can’t answer this question with a quick and simple answer. It’s a complicated topic because, even though WordPress is fairly secure out of the box, it gets a bad rap for being vulnerable to a range of issues; most of these issues are related to the fact that the platform wasn’t initially created as a platform for doing business.
On top of that, many WordPress users tend to make pretty bad choices when it comes to security, and they contribute to the myth that the platform is inherently unsafe for business use. This, added with the fact that WordPress is the most widely used content management system (CMS), may create some problems for the platform’s image as a secure one.
For example, the recent Hacked Website Report 2018 found that WordPress-powered websites accounted for 90 percent of all hacked CMS sites last year.
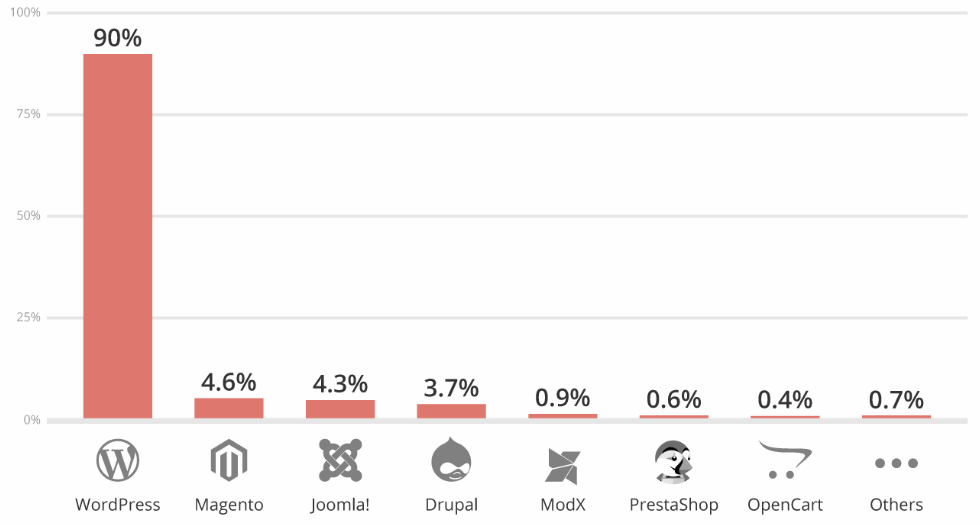
However, a closer look at the reasons why so many WordPress-powered websites were hacked reveals something interesting. According to the report, most of the vulnerabilities were caused by user-related reasons, including:
- A failure to update the system
- A lack of maintenance by webmasters
- Vulnerabilities in plugins and themes installed by website owners
- Misconfiguration issues.
These findings suggest that many of the security problems that give WordPress a bad reputation have nothing to do with the CMS. For example, as the report found, more than 36 percent of hacked websites based on WordPress had an outdated version of the system.
This mistake is quite common: in fact, the Reuters News website was hacked back in 2012 because of an old WordPress version that lacked the latest security patches that protected it from attacks. Apparently, the system sent the users at Reuters a lot of notifications about the newer version, but for some reason, they chose not to act.
“If organizations ignore those notifications and stay on an outdated version, then they put themselves at risk of these sorts of breaches,” Wall Street Journal quoted Mark Jaquith, one of the WordPress security experts, as saying.”
So, instead of suggesting that WordPress has some security shortcomings, findings like these rather mean that many of the platform’s users ignore essential security requirements, hoping that developers would take care of everything. Unfortunately, this is not the case because there’s no 100 percent secured CMS, so users should also take charge of the maintenance of their websites to ensure maximum security.
That’s why we’re going to review the latest WordPress security mersin escort advancements and methods in this article. Since you as a user of the system is responsible for keeping it secure and your business alive and thriving, we thought we’d give you everything you need to know to stay protected.
So, take a look at the following tips to lock down your website and keep hackers away.
WordPress Security Issues that You Need to Protect Your Website From
The following list contains many of the most important security issues that WordPress users face these days.
- Outdated System
- Brute Force Attacks
- Weak Passwords
- Inactive users
How to Secure Your WordPress Website
1. Always Update Your CMS:
We’ve already touched upon this issue above, but it deserves a separate section due to its prevalence. While it makes perfect sense to install updates to get the latest security patches from WordPress developers, many users of the CMS choose to avoid them because of many reasons (for example, many think that updates could undermine the stability of the system).
That’s why WordPress accounted for 36.7 percent of the infected CMS, according to Hacked Website Report 2019.
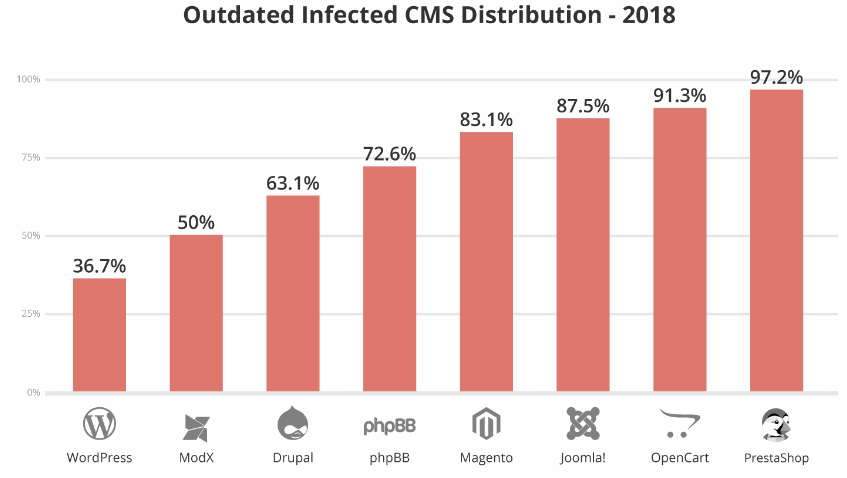
This finding once again proves that some owners of WordPress-powered websites are notorious for ignoring updates and exposing their businesses to avoidable risks. So, the solution here, although pretty simple, is also tremendously important for the success of your online business.
Install updates: Always install updates
So, the next time you see a notification about a new update released by WordPress developers, make sure to click on “Install.”
2. Techniques Against Brute Force Attacks
A brute force attack is one of the most popular methods for hacking a website because it’s one of the easiest ones. Simply explained, it’s a trial-and-error method that includes trying a plethora of usernames and passwords until some of them work, to gain access to a website.
Unfortunately, brute force attacks are on the rise; for example, their number has increased by 400 percent in 2017. Many of these attacks targeted websites in the finance industry where hackers could gain significant rewards, but any WordPress website is a potential target because of the login page.
So, there are many methods that you can use to defend your website here.
Introduce the Multi-factor Authentication (MFA):
MFA tries to increase security by adding an extra layer of protection, typically in the form of a login confirmation code sent to your phone or a prompt that you have to tap on a screen of your device. This means that if a hacker succeeds at stealing your login information during a brute force attack, they still won’t be able to access your website, because, well, they don’t have your phone.
MFA is a highly effective method for protecting user accounts; in fact, Google has recently introduced 2-step verification, or essentially MFA, to increase the security of Google user accounts. The company also teamed up with the University of California to assess the performance of MFA in preventing account takeovers, and here’s what they found.

As you can see, the method could be very effective at preventing hackers from getting access to your account, so consider introducing 2-step authentication on your WordPress website as well.
Install a Firewall Solution:
Blocking a brute force attack before it gets to the server is important to prevent crashes or website speed issues. One way to do this is to install a WordPress firewall plugin that evaluates the incoming traffic and prevents access for hackers.
There are two types of firewall solutions suitable for the job: application-level and DNS-level. The first respective type of plugin analyzes the traffic before loading WordPress scripts, thus minimizing potential damage from an attack. Next, the second respective option is more efficient because it prevents bad traffic from winding up on your website by routing it through your own cloud proxy servers.
3. Force Users to Come Up with Strong Passwords for Their Accounts
Also, remember that strong passwords are another way to reduce the risk of a brute force attack. While it may take some time for hackers to find out the passwords your users use to access their accounts, they can certainly do it.
There are two ways to make sure that all passwords used on your WordPress are secure. First, you can use secure generators like Random Password Generator to create complex password options for yourself. Second, you can also prevent your users from having weak passwords by installing a plugin called Force Strong Passwords.
4. Log Out Idle Users Automatically
Inactive and idle users are one well-known source of brute force attacks. When a logged in user stays inactive for a long period of time, it becomes possible for a hacker to get unauthorized access by running cookie or session hijacking. As a result, they can obtain login information and more.
This is a serious concern since a lot of people don’t really put much thought into this, especially if they are the only users on a website. By thinking that their website is insignificant for hackers or disregarding the importance of logging out, they’re giving hackers a chance to get login credentials.
Thankfully, there’s a plugin called Inactive Logout, and its name pretty much says it all: it enables the admin to change idle timeout time, thus eliminating inactive users from the site.
Also, you can add a “wake up!” message to the user, notifying that they will soon be logged out. So, by having a plugin controlling the idle time on your WordPress site, you can significantly reduce the risk of session or password hijacking.
5. Change Default WordPress Admin Login URL
The WordPress admin area is a popular target for brute force attacks. If hackers succeed at breaking your admin login data, chances are you’ll never regain control over your website and all the hard work you’ve invested in it would be lost. Once a hacker knows that your website is powered by WordPress, they immediately know that your login URL is www.yousite.com/wp-login.php.
One effective way to reduce the chance of someone hacking into your admin panel is to change the default admin login URL so the attackers won’t be able to find it. For that, you can install a plugin called WPS Hide Login.

It’s pretty straightforward to use and configure. For example, once you’ve installed it, a new option will appear under general settings, called “WPS Hide Login.” Click on it and you’ll open the tab of the plugin where you can change the admin login URL.
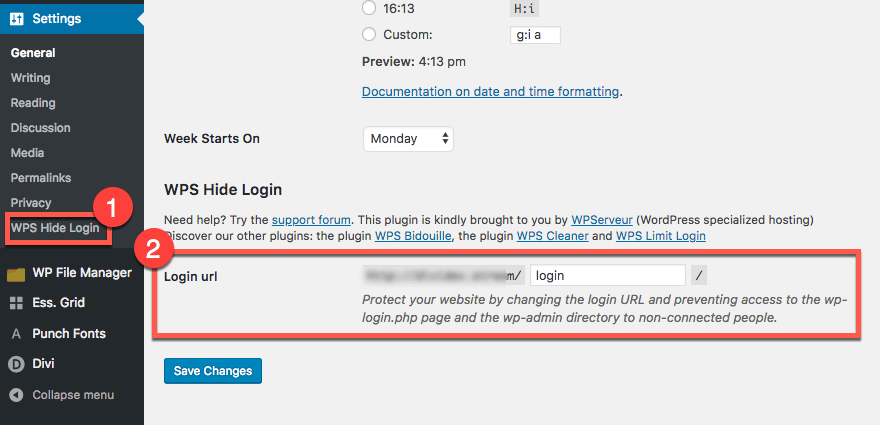
When you create a new URL and save the changes, non-connected Internet users won’t be able to access wp-login.php and wp-admin directory and get a 404 error page. Only those who are logged in are able to do that. Remember that you can put pretty much anything in the black space to make it a new URL, so feel free to let your imagination wild.
Changing the login URL with this plugin won’t make any changes to the website because it simply intercepts page requests from non-connected users.
6. Limit Login Attempts
Another way to lock down your WordPress admin login page and dramatically reduce the chance of getting hacked is to limit the number of times someone can try to log in. If a hacker launches a targeted attack on your website and tries to guess your login data, chances are high that they will succeed, given enough time. So, it’s your duty to deprive them of that chance by putting a limit in place.
Thankfully, limiting login attempts is very easy even if you’re not an experienced WordPress user. For example, all you have to do is install a plugin that lets you do just that. One good one is called WPS Limit Login, and it comes from the creators of the WPS Hide Login plugin introduced in the previous section.

It allows specifying a certain number of allowed failed login attempts before the admin panel is locked, as well as how long the lockdown lasts. It’s advised to allow only a few failed attempts, while you can set the blockage of a particular IP address at one hour. This will make conducting a successful brute force attack extremely difficult, and chances are that the hacker can stop trying.
7. Change WordPress Database Prefix
A WordPress installation creates eleven tables in the MySQL database, with all of them having the same default prefix: wp_ (wp_options, wp_users, wp_posts, wp_comments, etc.). The names of the databases describe their purpose; for example, wp_posts is where your blog posts are stored while wp_users is where you can find information about users.
Most WordPress users don’t change the prefix because they don’t know that hackers can exploit this to their advantage and get access to websites (this is called SQL injection vulnerability). SQL injection vulnerability provides the hacker with the ability to “inject” SQL code through an input that is accessible by users of the site and execute it using the SQL server where the eleven databases are stored.
To retrieve the private data of website users, a hacker can enter SQL code in a sign-up form instead of the email address. The website may execute the code and return the content inside wp_users to the hacker, thus creating all sorts of problems for the website owner. That is, of course, if the database table prefix is the default in your website.
To prevent SQL injection attacks and keep your data stored in the database safe, you can change the prefix by following these steps (before you do that, though, it’s highly recommended to back up the contents of the database):
- Open the WordPress root directory and find wp-config.php file
- Open it and find the prefix line, e.g. $table_prefix = ‘wp_”
- Change the prefix (letters, underscores, and numbers are allowed; for example, “wp_n1m7c42”
- Rename all table prefixes.
To reduce the risk of your site being hacked further, be sure to rename all of the WordPress database tables you have whose names begin with default values.
The last step here is to replace the old names of tables in the options table. To speed up this process, feel free to use the following SQL query:
SELECT * FROM ‘wp_n1m7c42_options’ WHERE ‘option_name’ LIKE ‘%wp_%’
As you can see, the query seeks to find the default value – ‘wp_’ and replace them with the example used earlier in this section: wp_n1m7c42.”
The last step here is to double-check everything to make sure that your database is working perfectly.
8. Monitor Admin Activity
If your WordPress website has multiple users, it’s totally worth tracking their activity to see what they’re doing as well as spots such security issues like unauthorized users. For example, if an admin adds a user that does something suspicious or commits an unauthorized action themselves, you’ll be able to identify that.
Since WordPress doesn’t have default plugins for that, you need to install a plugin like WP Security Audit Log.
It provides real-time user monitoring and enables to identify of the following changes:
- Menu and widget changes
- Post and page changes
- Category and tag changes
- User activity, including login, logout, terminating other activity sessions and failed logins
- Registration of new users, deletion of existing users, and modifying their accounts
- Changes in user profiles, including display name, role, email, and password
- WordPress settings changes
- Changes in themes or plugins
- Site file changes
In other words, you have an opportunity to track pretty much everything that other users do on your website, which is exactly what you need to reduce the risk of someone undermining its security. If someone does something that they’re not supposed to, you’ll know about that action quickly.
9. Hide the UserName
One surefire way to give access to your WordPress admin account to hackers is to let them know the username. Here’s the problem: when you create a new user in WordPress, the CMS uses it to rewrite the URLs to the pages that have content created by that user (for example, these could be pages written by a specific author).
As a result, a random visitor – that means a hacker, too – can see the user name in the address bar in their browser. For example, let’s suppose that your username is peter johnson. Here’s what the page with your content will look like in the address bar:
www.example/author/peterjohnson
With this information, the task of hacking into the admin panel becomes much easier because they have half of the information required to succeed. So, you need to hide it by following these steps:
- Go to the user’s profile page and check whether First Name and Last Name fields are filled
- Click on Display Name Publicly to view the drop-down menu where you can choose how your username appears on pages. Here, it’s important to select something different from your admin username
- Change the user_nicename entry for the changed username from the database. To do that, you need to go to the Databases section and log in to your hosting provider
- Click on phpMyAdmin, select your database, and go to the wp_users table (please note that the name of the table could be different if you followed the above tip and changed the database prefix)
- The first column in the table is Edit, click on it
- Change the user-nickname to a name that is different than the current username
- Find the Go button below the table and click on it to save the changes you just made.
Another way to change the username is by issuing a special command in MySQL. For example, let’s once again suppose that you have an account with the following information: username: peter johnson, First Name: Peter, Last Name Johnson.
Here’s the command:
UPDATE `wpdb`.`wp_users` SET `user_nicename` = ' peter-johnson' WHERE `wp_users`.`ID` =3.
As with pretty much anything else with WordPress, you can also use a special plugin for hiding your username. For example, the smart Archive Page Remove can help you remove automatically generated archive pages (Author-based, category-based, tag-based, etc.) for posts.
If someone tries to access the removed pages, they will get the 404 error.
10. Always Use Secure Hosting
Poor-quality web hosting is a major reason why WordPress websites get hacked. Indeed, the foundation on which you run your website is critically important for your security because the provider also plays a decisive role in preventing and identifying attacks from hackers.
Since the selection of hosting options, today is quite large, you should look for ones that provide the following features that maximize protection:
- Uptime monitoring
- Detection and mitigation of DDOS attacks with DDoS protection services
- Intrusion detection systems that identify suspicious activity
- The requirement of only encrypted connections (SSH and SFTP) for direct site access
- Automatic ban of IP addresses after more than five failed attempts to log in
- Restrictions that prohibit to run PHP in common directories.
If your existing hosting provider doesn’t have some of these features or lacks security-related support, you should consider moving to a more secure solution to increase the security of your website.
“Moreover, keep in mind that security-related features shouldn’t affect the performance of your site,” says Adam Morrison, a web security expert from Trust My Paper. “You know very well that Internet users don’t like to wait for a website to load.”
11. Have Google Let You Know About New Pages on Your Website
This is an easy and effective technique that you can use right now. In some cases, hackers add new pages to a website that an owner can’t see in the front or backend, so they can continue their activities without anyone knowing about it. However, there’s one way to detect new pages that were added without an admin’s permission: Google Alerts.
Since new pages get indexed in Google, you can set an alert to know if someone is messing up with your website without your permission. All you have to do is go to Google Alerts, add your site in the top bar, select additional options such as language, and set How Often to As-it-happens. Also, select All Results in How Many fields because you need to receive all indexed results.
Now, you’ll get quick notifications when a new page from your website gets indexed by Google.
12. Protect Your Website Effectively and Proactively
Of course, we can’t cover every single WordPress security technique here, but these are definitely the ones that you should consider implementing first because they help to mitigate and avoid the most common brute force attacks. Also, we hope this guide helped you to understand the significance of staying up-to-date with WordPress security solutions and being an active player when it comes to protecting your online business from hackers.
Even though WordPress-powered websites comprise a large part of those that were hacked last year, it’s safe to assume that many attacks could have been mitigated if the owners followed the latest security recommendations. So, now you’re in a much better position to start strengthening the security of your website.
I hope this guide helps you secure your WordPress site if you have any questions please feel free to ask them in the comments section below.
If issues like these are not something you want to be dealing it, take a look at our managed WordPress hosting plans that let you run your business without having to worry about your server or web hosting.
![12 Simple Tricks for WordPress Security- [Keep WordPress Safe in 2019]](https://host4geeks.com/wp-content/uploads/2019/06/wordpress-security-header-image-2-1-1536x1034-2.jpg)
