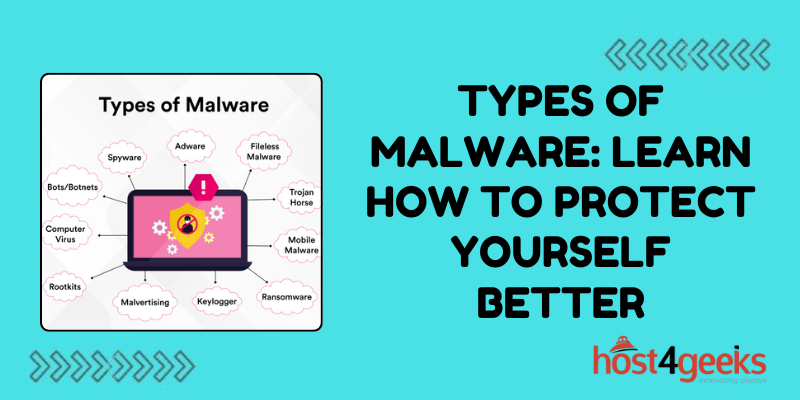
In the vast realm of cyber security, one term stands out prominently: malware. Malware, short for malicious software, encompasses a broad spectrum of threats designed to infiltrate, disrupt, damage, or gain unauthorized access to computer systems and networks.
Understanding the types of malware: learn how to protect yourself better is crucial for both beginners and experts in cyber security, as it empowers individuals and organizations to fortify their defenses against these insidious digital threats.
Significance of Understanding Types of Malware
The significance of comprehending various types of malware cannot be overstated in today’s interconnected digital landscape. As technology advances, so do the sophistication and diversity of malware threats.
Each type of malware employs distinct techniques and exploits vulnerabilities in different ways. By familiarizing oneself with these variations, users can adopt proactive measures to mitigate risks and safeguard their digital assets.
For beginners, recognizing common types of malware lays the foundation for developing basic cyber security awareness.
It enables them to identify potential threats and take essential precautions to protect their devices and personal information.
On the other hand, for seasoned cyber security professionals, a deep understanding of malware types is indispensable for devising robust defense strategies, conducting thorough risk assessments and implementing targeted security measures tailored to specific threats.
Explaining Types of Malware for Beginners
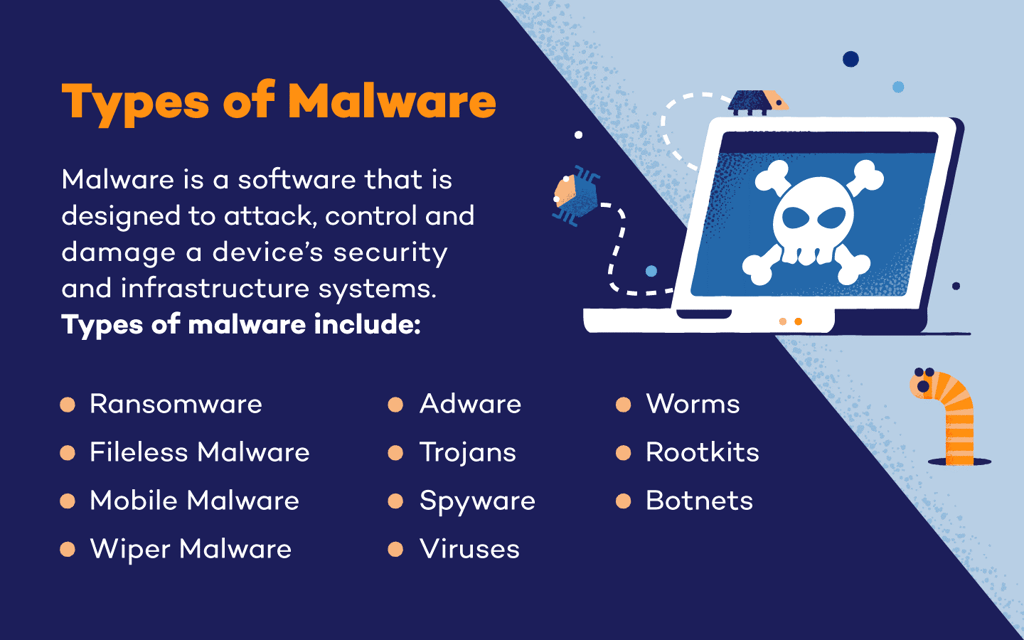
1. Viruses:
Viruses are perhaps the most well-known type of malware. They attach themselves to legitimate programs or files and replicate when the infected file is executed.
Viruses can spread rapidly and cause widespread damage by corrupting or deleting files, disrupting system functionality, and even rendering the entire system inoperable.
2. Worms:
Worms are self-replicating malware that can spread across networks without human intervention. Unlike viruses, worms do not require a host program to propagate.
They exploit vulnerabilities in network protocols to infiltrate computers and proliferate, often causing network congestion, system slowdowns, or distributed denial-of-service (DDoS) attacks.
3. Trojans:
Trojans disguise themselves as legitimate software to deceive users into installing them.
Once activated, Trojans can perform a variety of malicious activities, such as stealing sensitive information, creating backdoors for remote access, or downloading additional malware onto the system.
They often masquerade as harmless applications or files, making them particularly deceptive.
4. Ransom ware:
Ransom ware encrypts files or locks users out of their systems, demanding a ransom payment in exchange for restoring access.
This type of malware has become increasingly prevalent and devastating, targeting individuals, businesses, and even critical infrastructure.
Ransom ware attacks can result in significant financial losses, data breaches, and operational disruptions.
5. Spyware:
Spyware clandestinely monitors users’ activities, collects sensitive information, and transmits it to malicious actors without their consent.
It can capture keystrokes, log browsing habits, harvest login credentials, and even activate webcams or microphones for surveillance purposes.
Spyware poses a serious threat to privacy and confidentiality, compromising personal and corporate data.
6. Adware:
Adware displays intrusive advertisements or redirects users to malicious websites in an attempt to generate revenue for the attacker.
While not inherently harmful, adware can degrade system performance, diminish user experience, and expose individuals to further malware infections. It often accompanies free software downloads or deceptive online ads.
Explaining Protection Strategies for Beginners and Experts
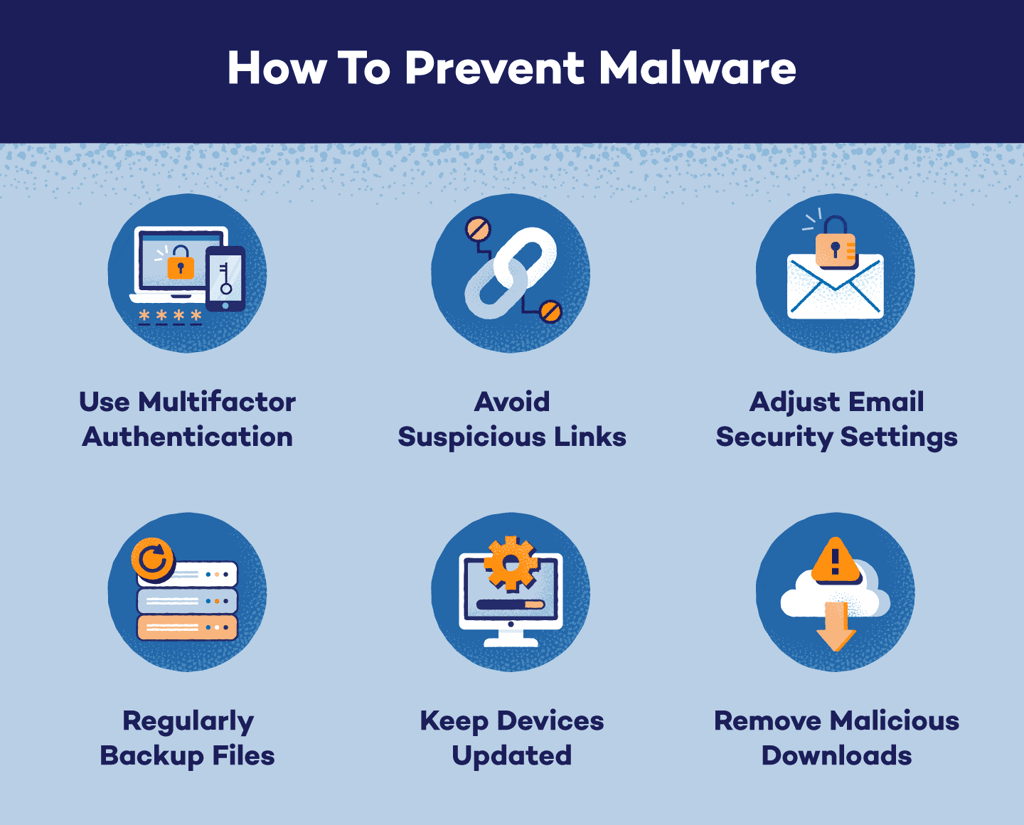
1. Keep Software Updated:
Regularly update operating systems, applications, and antivirus software to patch security vulnerabilities and protect against known exploits. Both beginners and experts should prioritize software updates as a fundamental defense measure.
2. Use Antivirus/Antimalware Software:
Install reputable antivirus or antimalware software and keep it up to date. Configure it to perform regular scans and real-time protection to detect and remove malware threats effectively.
3. Exercise Caution Online:
Practice safe browsing habits, avoid clicking on suspicious links or downloading files from untrusted sources, and be wary of unsolicited emails or attachments.
Beginners should learn to recognize common phishing tactics, while experts should stay informed about emerging threat vectors.
4. Enable Firewalls:
Activate firewalls on both individual devices and network routers to block unauthorized access and prevent malware from infiltrating your system.
Configure firewall settings to filter incoming and outgoing traffic based on predefined rules.
5. Backup Data Regularly:
Implement a robust backup strategy to safeguard critical data against ransomware attacks and other forms of data loss. Store backups on secure, offline or offsite locations to prevent them from being compromised by malware.
6. Employ Behavior-Based Detection:
Utilize advanced security solutions that employ behavior-based detection techniques to identify and mitigate previously unseen malware threats.
These solutions analyze software behavior patterns and detect suspicious activities indicative of malware infections.
7. Educate Users:
Educate both end users and IT professionals about cybersecurity best practices, including recognizing signs of malware infection, responding to security incidents, and adhering to organizational security policies.
Continuous training and awareness programs are essential for strengthening the human firewall against evolving threats.
Conclusion:
In conclusion, understanding the types of malware: learn how to protect yourself better and implementing proactive protection measures are critical for safeguarding against digital threats in today’s interconnected world.
Whether you’re a novice or an expert in cybersecurity, staying informed, adopting best practices, and remaining vigilant are paramount for defending against malware attacks and preserving the integrity and security of digital assets.
By empowering individuals and organizations with the knowledge and tools to combat malware effectively, we can collectively create a safer and more resilient cyber environment for all.