In an increasingly digital world, the security of your server infrastructure is paramount. For businesses and tech enthusiasts alike, Linux dedicated servers offer a robust and flexible platform for hosting websites, applications, and databases. However, with great power comes great responsibility.
Securing a Linux dedicated server requires a multi-faceted approach to protect against cyber threats and ensure seamless operations. This guide delves into the comprehensive steps to secure your Linux server while exploring other critical aspects, including the pros and cons of using a Linux dedicated server.
Aspects of Linux Dedicated Servers
1. Performance and Resources
- High Performance: Linux dedicated servers offer powerful performance with dedicated resources, ensuring that your applications run smoothly without interference from other users.
- Scalability: These servers can be easily scaled to meet the growing demands of your business by upgrading hardware or optimizing configurations.
2. Customization and Control
- Full Root Access: With full root access, you have complete control over the server, allowing you to install and configure software as per your requirements.
- Customizable Environment: Linux servers support various distributions (e.g., Ubuntu, CentOS, Debian), enabling you to choose the environment that best suits your needs.
3. Security
- Robust Security Features: Linux is known for its strong security architecture, with features like user permissions, SELinux, and iptables to help protect your server.
- Community Support: The extensive Linux community provides a wealth of knowledge, resources, and tools to help maintain and enhance server security.
4. Cost-Effectiveness
- Open Source: Linux is open-source, meaning you can use it without paying for a license, reducing the overall cost of ownership.
- Efficient Resource Management: Linux is known for its efficient use of resources, which can translate to cost savings on hardware and energy consumption.
5. Reliability and Uptime
- Stability: Linux servers are renowned for their stability and reliability, with minimal downtime, making them ideal for mission-critical applications.
- Long-Term Support (LTS): Many Linux distributions offer LTS versions, providing extended support and updates, ensuring long-term reliability.
Securing a Linux dedicated server involves multiple layers of protection to safeguard the system from unauthorized access, malware, and other potential threats.
Here are detailed steps and best practices to secure your Linux dedicated server:
1. Initial Server Setup
- Update the System: Ensure all software is up-to-date.

- Create a New User: Avoid using the root account for regular use.

- Disable Root Login: Edit the SSH configuration file.
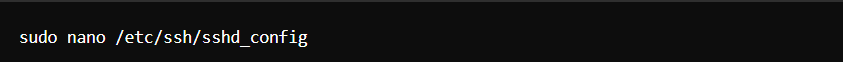
Set PermitRootLogin to no.
2. Secure SSH
- Change the Default SSH Port: Avoid using port 22.
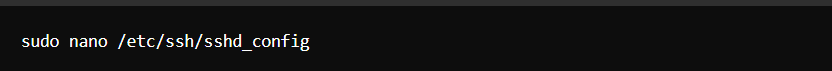
Change Port 22 to another number (e.g., Port 2222).
- Use SSH Key Authentication: Generate SSH keys and disable password authentication.

Edit the SSH configuration file.
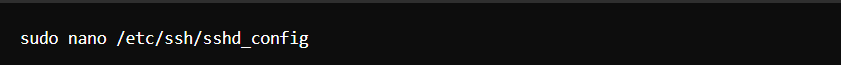
Set PasswordAuthentication to no.
3. Firewall Configuration
- Enable and Configure UFW (Uncomplicated Firewall):
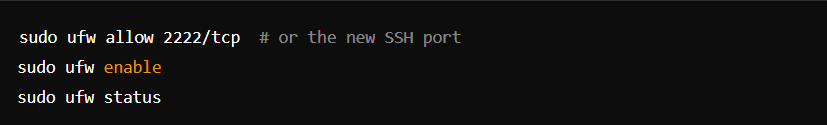
4. Intrusion Detection and Prevention
- Install Fail2Ban: Protect against brute-force attacks.
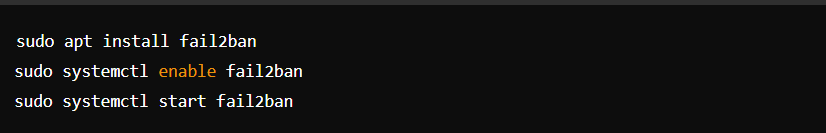
Configure Fail2Ban by editing jail.local:

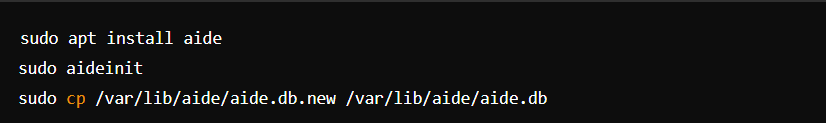
- Install and Configure an IDS: Tools like AIDE or Tripwire.
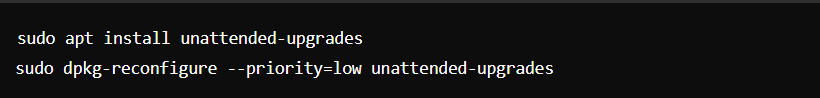
5. Security Updates and Patching
- Enable Automatic Updates: Use unattended-upgrades.
6. Application Security
- Web Server Hardening: If using Apache or Nginx, apply security configurations.
- For Apache:
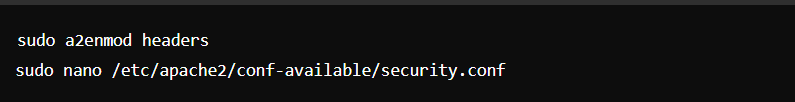
Configure as necessary.
- For Nginx:
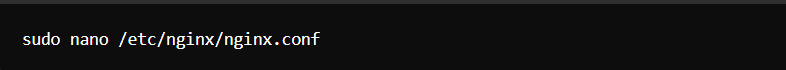
Add security headers and settings.
- Database Security: For MySQL/MariaDB, secure the installation.

7. Monitoring and Logging
- Set Up System Logging: Ensure rsyslog is installed and configured.
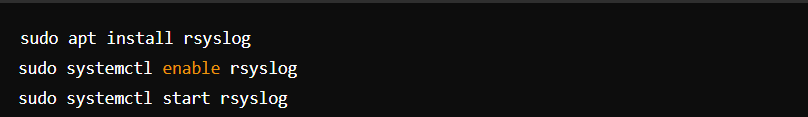
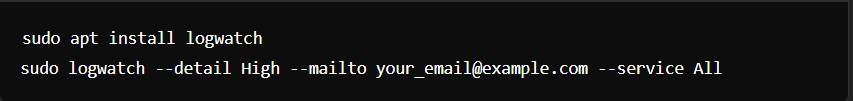
- Log Monitoring: Use tools like Logwatch or logcheck.
8. Access Control and User Management
- Use sudo for Privileged Commands: Ensure only authorized users have sudo access.
![]()
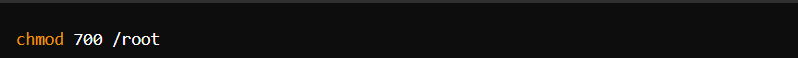
- Limit User Access: Restrict access to sensitive files and directories using proper permissions.
9. Backup and Recovery
- Regular Backups: Use tools like rsync, tar, or dedicated backup software.
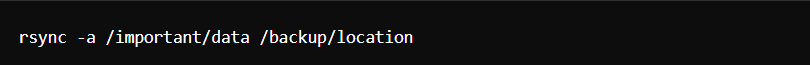
- Test Backups: Regularly test your backups to ensure they can be restored.
10. Network Security
- Disable Unused Network Services: Turn off services that are not in use.

- Install and Configure a VPN: Use OpenVPN or WireGuard for secure remote access.
11. Additional Security Measures
- Install Anti-Malware Tools: Use ClamAV or similar tools.

- Secure DNS: Use a trusted DNS provider and consider DNSSEC.
12. Security Audits and Penetration Testing
- Regular Audits: Perform regular security audits using tools like Lynis.
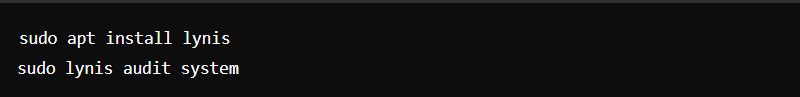
- Penetration Testing: Regularly test your server’s security with tools like Metasploit.
By implementing these measures, you can significantly enhance the security of your Linux dedicated server, reducing the risk of breaches and ensuring the integrity and availability of your services.
Pros and Cons of Linux Dedicated Servers
Pros
- Performance: With dedicated resources, Linux servers provide excellent performance, essential for high-traffic websites and resource-intensive applications.
- Security: Linux offers advanced security features, reducing the risk of unauthorized access and cyber threats.
- Cost-Effective: Being open-source, Linux reduces software licensing costs and offers efficient resource management.
- Customization: Full root access and a variety of distributions allow for a highly customizable server environment.
- Stability and Uptime: Known for their reliability, Linux servers ensure consistent uptime and stability.
Cons
- Complexity: Managing a Linux server can be complex, especially for users without a strong background in Linux administration.
- Learning Curve: For those unfamiliar with Linux, there is a steep learning curve to effectively manage and secure the server.
- Support: While the community support is extensive, professional support might be limited compared to commercial operating systems like Windows Server.
- Compatibility Issues: Some commercial software may not be compatible with Linux, requiring alternatives or workarounds.
- Maintenance: Regular maintenance, updates, and security patches are necessary to keep the server secure and running smoothly, requiring time and expertise.
Conclusion
A Linux dedicated server is a powerful tool for any organization seeking high performance, security, and customization. However, securing this environment is critical to protect against evolving cyber threats.
By following the detailed steps and best practices outlined in this guide, you can ensure your Linux server remains secure, efficient, and reliable. Understanding the benefits and challenges associated with Linux dedicated servers will help you make informed decisions and optimize your server infrastructure to meet your specific needs.

