The “Target Principal Name is Incorrect” error is one of the most disruptive and potentially damaging errors that can occur in SQL Server operations. When this error rears its head, it grinds databases and applications to a halt, carrying risks of connectivity issues, data corruption, and even data loss if not addressed promptly.
So, if you’ve encountered the “Target Principal Name is Incorrect” Error in SQL Server, you’re not alone, and we’re here to help you. In this blog post, we will walk you through the steps to identify the root cause of the error and provide you with effective solutions to resolve it.
We will peel back the layers of this error to understand why it occurs, how it impacts SQL Server functionality, and the meticulous troubleshooting required to resolve it. Armed with insights from expert tips, you’ll not only be equipped to address this error when it strikes but also implement bulletproof preventive measures to avoid future occurrences.
Join us as we traverse the landscape of this notorious SQL Server error, and emerge with skills to counter it effectively. Whether you’re a database administrator, a developer, or a SQL Server enthusiast, this guide is designed to equip you with the knowledge and tools you need to tackle this issue head-on. So, let’s dive in and conquer the “Target Principal Name is Incorrect” error together!
The Basics: Understanding the”Target Principal Name is Incorrect” Error
The “Target Principal Name is Incorrect” error is a common issue in SQL Server. It occurs when a user tries to connect to a SQL Server instance using a domain account and receives the following error message: “Login failed. The target principal name is incorrect. Cannot generate SSPI context.” This error message indicates that the SQL Server service cannot locate a domain controller to authenticate the user’s account.
Some common target services that trigger this error during authentication include Active Directory Domain Services, remote SQL Server instances, file shares, and more. We’ll explore the intricacies of service principal names and authentication mechanisms later.
Key Scenarios Triggering This Error
In dynamic and distributed SQL Server deployments, numerous factors can conspire to produce sudden “Target Principal” failures. On the surface unexpected, recognizing common troubleshooting scenarios is key to rapid resolutions though.
Scenario 1: Renaming a SQL Server
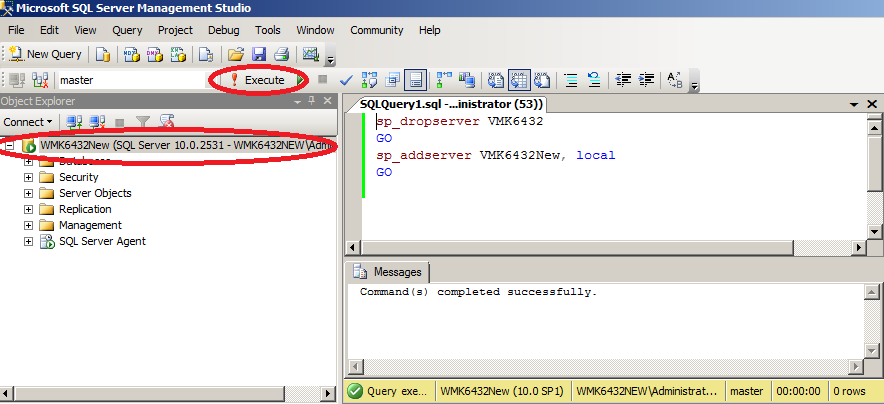
Renaming a SQL Server can cause the “Target Principal Name is Incorrect” error. When you rename a SQL Server, the SPN for the SQL Server instance becomes invalid. To troubleshoot this issue, you can use the SETSPN command-line tool to check if the SPN is valid. If the SPN is invalid, you can use the SETSPN tool to re-register the SPN.
Scenario 2: Moving a SQL Server to a New Domain
Moving an SQL Server to a new domain can also cause the “Target Principal Name is Incorrect” error. To troubleshoot this issue, you should check the SQL Server service account and verify that it has the appropriate permissions to access the domain controller. You can also use the SETSPN tool to check if the SPN is valid.
Scenario 3: Changing SQL Server Service Account
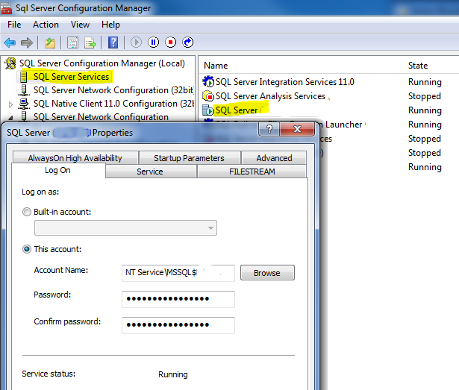
Changing the SQL Server service account can also cause the “Target Principal Name is Incorrect” error. To troubleshoot this issue, you should check the SQL Server service account and verify that it has the appropriate permissions to access the domain controller. You can also use the SETSPN tool to check if the SPN is valid.
Scenario 4: Restoring a Database to a Different Server
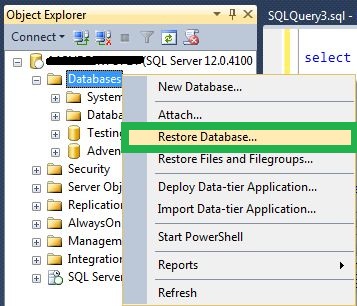
Restoring a database to a different server can cause the “Target Principal Name is Incorrect” error if the database owner (dbo) is not valid on the new server. To troubleshoot this issue, you should check the ownership of the database and ensure that the dbo is a valid user on the new server. You can also use the sp_changedbowner stored procedure to change the database owner if necessary.
Scenario 5: SQL Server Authentication instead of Windows Authentication

Using SQL Server Authentication instead of Windows Authentication can cause the “Target Principal Name is Incorrect” error. To troubleshoot this issue, you should check the SQL Server service account and verify that it has the appropriate permissions to access the domain controller. You can also configure the SQL Server to use Windows Authentication instead of SQL Server Authentication.
When SQL Server instances are moved or renamed, the associated SPNs require meticulous updates to realign mappings. Any discrepancies lead to authentication failures and this dreaded error. Network, DNS, or domain controller issues can also prevent proper SPN mapping and trigger authentication errors.
The Root Causes
At its core, the “Target Principal Name is Incorrect” error indicates one key problem – the SQL Server is unable to authenticate with the intended service principal as expected. The reasons for failed authentication manifest in different forms:
Authentication Issues:
Flaws in authentication settings, account permissions, or encryption cause authentication handshakes to fail, triggering the error. Issues with domain trust relationships also lead to authentication problems.
Mismatched SPNs:
The SPN that the SQL Server expects does not match the actual SPN of the service, due to incorrect mapping, replication lags, etc. leading to failed connections.
Network Configuration Issues:
Connectivity issues, DNS resolution failures, or firewall rules block SQL Server from accessing the required service principal, resulting in the error.
Underlying all these root causes is a break in the communication channels and relationships between SQL Server, associated services, and Active Directory. Rectifying the specific area of breakdown is key.
Impact on SQL Server Operations
Much more than an isolated error, “Incorrect Target Principal” warnings have far-reaching implications that require urgent troubleshooting. Depending on the environment, disruption across critical production operations can occur rapidly:
Session Failures and Connectivity Issues: Active database sessions will fail upon executing transactions that require principal verification. Connections will also refuse user and application access attempts signaling principal problems. Operational disturbances follow until corrected.
Transactional Integrity Risks: Fundamental SQL services including locking, logging, backup/restore, high availability replication, etc. depend on maintained principal access between related components. Otherwise, transaction loss occurs.
Application and Reporting Cease: Applications, scripts, reporting – any programmatic SQL Server interation ceases without proper principal permissions. Dashboards, ETL, and more become dead in the water during outages.
Data Corruption Potential: Most concerning, access denials mean critical jobs, processes, and backups could fail leading to actual data corruption or loss scenarios. Prevention is crucial!
The degree of potential disruption is far-reaching and diverse across SQL Server installations yet avoiding downtime is pivotal.
Resolving the “Target Principal Name is Incorrect” Error
If you encounter the “Target Principal Name is Incorrect” error in SQL Server, there are several resolving steps you can take to resolve the issue. Some of them have already been discussed briefly above. However, in this section, we will discuss each step in detail.
Check SQL Server Configuration Settings
The first step in troubleshooting the “Target Principal Name is Incorrect” error is to check the SQL Server configuration settings. You should verify that the SQL Server is configured to use Windows Authentication and that the SQL Server service account has the appropriate permissions to access the domain controller.
Verify the SQL Server Service Account
You should also verify the SQL Server service account and ensure that it has the appropriate permissions to access the domain controller. You can check the SQL Server service account by using the SQL Server Configuration Manager.
Verify SQL Server Authentication and Permissions:
If you are using SQL Server Authentication, you should verify that the login and password are correct. You should also check the SQL Server logins and ensure that the appropriate permissions are granted to the user.
Check the Domain Trust Relationship:
If you are encountering the “Target Principal Name is Incorrect” error when connecting to an SQL Server in a different domain, you should check the domain trust relationship. You should verify that the two domains have a trust relationship established and that the trust relationship is functional.
Check the DNS Configuration:
You should also check the DNS configuration and ensure that the SQL Server hostname and IP address are correctly registered in DNS. You can use the nslookup command to verify the DNS configuration.
Check the SPN (Service Principal Name) Configuration
The SPN is a unique identifier for a SQL Server instance. If the SPN is invalid, it can cause the “Target Principal Name is Incorrect” error. You can use the SETSPN tool to check the SPN configuration and re-register the SPN if necessary.
Use the SQL Server Configuration Manager
You can use the SQL Server Configuration Manager to troubleshoot the “Target Principal Name is Incorrect” error. The SQL Server Configuration Manager provides a graphical interface to configure and manage SQL Server services and settings.
Check the SQL Server Error Logs
You should also check the SQL Server error logs for any error messages related to the “Target Principal Name is Incorrect” error. The error logs can provide valuable information to help you troubleshoot the issue.
Service Principal Names (SPN) in Detail
With SQL Server’s own authentication flows confirmed as functional, attention shifts to the Service Principal Names presented by client applications when initiating connectivity.
You might be wondering what role SPNs play, and how can incorrect configurations lead to the “Target Principal Name is Incorrect” error.
If the SPN in the client’s login request does not precisely match what the server expects, rejections occur. Let’s decode this critical identifier at the heart of the authentication dance.
Demystifying SPNs
In Active Directory domains, Service Principal Names serve as unique identifiers for a service instance, forming the basis for Kerberos authentication. Breaking down the composition of a valid SPN sheds light on the registration requirements:
- Service Class: A logical name identifying the class of service (e.g. MSSQLSvc for SQL)
- FQDN: The full DNS domain name of the server (e.g. SQL01.corp.contoso.com)
- Instance Name: Optional named instance if connecting to non-defaults (e.g. MSSQLSERVER)
Thus an SPN uniquely pins an account identity to a specific SQL Server instance on the network. Under the hood, the Windows login credentials are tied one-to-one with a registered SPN through a process called Active Directory delegation. Correct SPN registrations are crucial for successful Kerberos logins.
Causes of Mismatched SPNs
With SPNs acting as virtual login names for services, the “incorrect principal name” error surfaces whenever:
- The SPN presented by client does NOT exist or resolve to the target SQL Server resource
- The client’s SPN matches a different account than SQL Server expects
- There exist duplicate, conflicting SPNs
The following scenarios illustrate how seemingly innocuous discrepancies in SPN registrations can sabotage authentication:
DNS Changes Not Reflected: If the AD DNS name of a server changes, but associated SPNs still reference the old name, connectivity breaks for applications using the new name. Lingering stale SPNs must get realigned with refreshed DNS entries.
Duplicate SPNs: When migrating SQL instances between servers, orphaned SPNs referencing old server names often remain alongside new SPNs. These duplicates confuse logins by matching multiple identities to the same credentials.
Failed Cluster Node SPNs: For failover clusters, SPNs only registered on active nodes may fail to follow SQL instances as they move during failovers, causing authentication rejections from nodes where SPNs are missing.
To resolve SPN mismatches, a careful audit of registered names compared to DNS entries and cluster configurations is needed before diagnosing network issues.
Now let’s shift gears to longer term resolution
Expert Tips for Prevention
Dealing with authentication errors is part of the balancer act for multi-tasking DBAs overseeing complex SQL estates. However painful outages sting in the present though, and prevention is key for lasting stability ahead. Here are pro tips from industry experts on shoring up defenses:
Tighten up Active Directory Permissions
Most authentication issues stem from overly loose AD security models. By enforcing the separation of duties through precise privilege assignment only to specific service accounts, uncertainties around access can be eliminated. Treat AD permissions carefully as the crown jewels defending the kingdom.
Standardize on Managed Service Accounts
Legacy SQL instance installations often have extremely dated local service accounts defined that pose security risks. Newer Managed Service Accounts centralize password management through AD itself, auto-renewing credentials to prevent expiration surprises that would break trust chains.
Register SPNs Automatically
Since SPN mismatches cause so many issues, manually registering them invites eventual drift between DNS names and service identities. Enforce consistency by enabling automatic SPN registrations via group policy to remove human errors from the equation.
Configure Periodic AD Replication Checks
Stale or divergent data among domain controllers from lagging AD sync failures is an easily overlooked yet highly destructive scenario. Configure monitoring tools to catch replication issues fast before harm is done.
Simulate Failures Through Chaos Testing
Unpredictable edge cases tend to surface during periods of stress like failovers, workload spikes, or network faults. Intentionally inject failures through chaos testing toolkits to observe and remediate authentication reliability gaps.
Adopting institutional safeguards helps sustain the gains from past incident response wins.
Common Misconfiguration Pitfalls
Hopefully, by now you feel empowered in your authentication troubleshooting and prevention repertoire through the tips and steps discussed above. While no systems are bulletproof though, avoiding some well-known SQL Server misconfiguration pitfalls will at least help dodge unnecessary self-inflicted headaches:
- Never use production data in non-production environments. Seeding user emails or real transactions outside internal systems spawns GDPR violations.
- Avoid enabling TCP/IP connections on public listener interfaces. Lockdown connectivity through Azure NSGs instead with restricted subnet access.
- Never mix privileged domain admin tasks on SQL Server boxes. Install admin tools on dedicated secured workstations only.
- Don’t rely solely on default database recovery models without testing whether backups actually work. Validate restores regularly!
- Never deploy unsupported TLS versions. Only enable TLS 1.2+ or risk crypto protocol downgrade attacks stealing credentials.
Conclusion:
The “target principal name is incorrect” error can stop you in your tracks when trying to connect to SQL Server, but with the right troubleshooting approach the issue can usually be resolved.
As outlined in the guide above, this error can be caused by several factors, including server name changes, domain account issues, and SPN configuration issues.
To troubleshoot the issue, you should check the SQL Server configuration settings, verify the SQL Server service account, check the domain trust relationship, and use the SQL Server Configuration Manager.
Once you have identified the cause of the error, you can use several options to fix the issue, including changing the SQL Server name, adding a new domain account, fixing the existing domain account, reconfiguring the SPN, or using the SQL Server Configuration Manager.
With methodical verification and a process of elimination to isolate the specific cause, the “target principal name is incorrect” error can typically be fixed and allow normal operations to resume.
FAQs (Frequently Asked Questions) About “Target Principal Name is Incorrect”
Q: I’ve used contained database users in my SQL Server databases. Could this cause the “Target Principal” error?
A: Yes, misconfigurations with contained users can manifest as authentication failures. Ensure the authentication setting is not conflicting between the user and database levels. Test connectivity with a sysadmin account.
Q: How to proactively monitor and detect this error before disruptions?
A: Enable SQL Server Agent alerts for Login failed events. Trace Logon and Logoff events to capture failure trends. Monitor DNS, domain controller, and SQL Server logs with a centralized tool to surface errors early.
Q: Does this error impact only my application or others too?
A: If the root cause is systemic like DNS or AD issues, all applications and database access could fail. Connection strings referencing the principal will log errors. Custom app problems indicate isolated misconfigurations.
Q: What if recommended troubleshooting does not resolve the error?
A: As a last resort, manually delete and recreate the SQL Server service account in AD. Test connectivity after systematically granting permissions back. Rebuild trust relationships if on disparate domains.
Q: Where to find Microsoft’s technical guidance on this error?
A: Microsoft has in-depth technical guidance on troubleshooting SQL Server error 4060 which corresponds to the “Target Principal Name” error message.